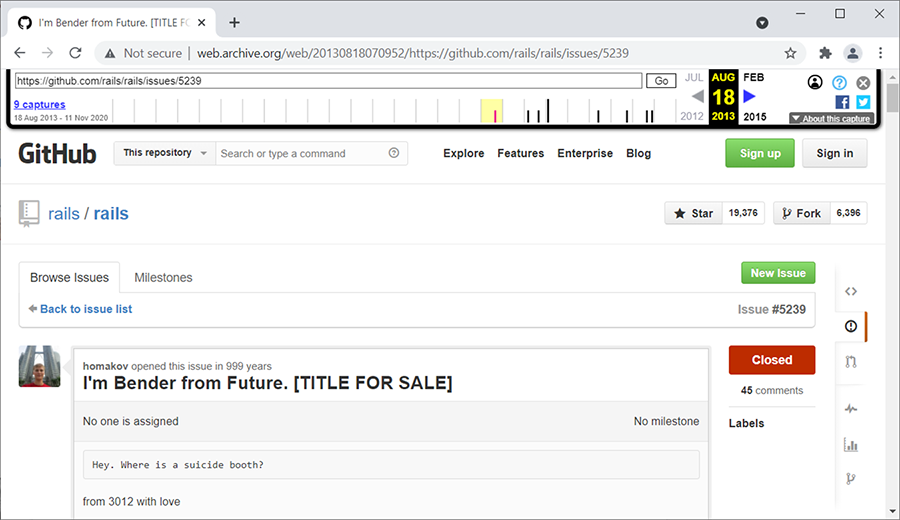
In 2012, Russian developer Egor Homakov started a discussion on the GitHub issue tracker for the Ruby on Rails framework (if you’re interested, here is the whole thread: https://github.com/rails/rails/issues/5228). He was worried about a specific attack called mass assignment, and whether Ruby on Rails should change its default behavior to prevent developers from falling into this trap. Not happy with the arguably stern replies he got, he searched and found a mass assignment security issue in GitHub (which, in turn, has been developed in Ruby on Rails). As a result, he managed to grant himself full privileges for the Ruby on Rails project on GitHub. To make it obvious to others that he was indeed able to exploit such a vulnerability, he created a very interesting issue in the bug tracker. The issue has since been updated, but figure 5.1 shows an archived version (the URL of the issue is https://github.com/rails/rails/issues/5239, and the screenshot shows a version from 2013, using Internet Archive’s Wayback Machine: http://web.archive.org/web/20130818070952/https://github.com/rails/rails/issues/5239).
chapter five