Chapter 4. Managing security
This chapter covers
- Introducing AWS Identity and Access Management
- Writing policies to allow or deny access to AWS resources
- Using policy variables to make policies more flexible
- Assuming roles to avoid the use of hard-coded AWS credentials
- Using roles with AWS Lambda functions
In the previous chapters, you created your first functions. At first you used those functions directly, using the AWS Lambda interface from the command line. Later, you exposed those functions via a web API provided by the Amazon API Gateway.
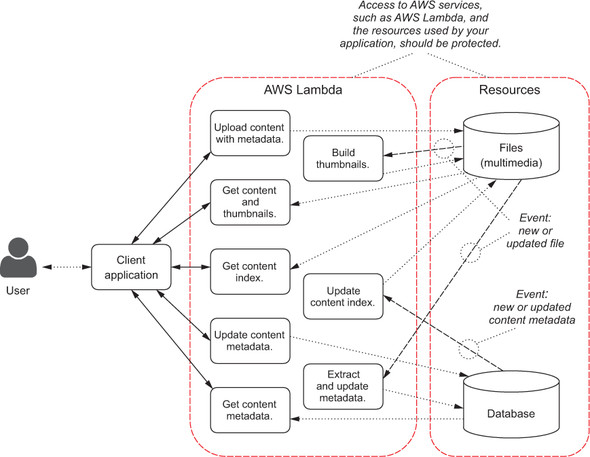
This chapter introduces the security framework provided by AWS, mostly based on AWS Identity and Access Management (IAM). You’ll learn how to protect your functions and applications implemented using AWS Lambda and (optionally) the Amazon API Gateway. As an example, any interaction with AWS services, such as AWS Lambda and the resources used by your application, must be protected to avoid unauthorized access (figure 4.1). We’ll also look back at the functions we created earlier to see how security was managed there.