In the last chapter we examined the networking primitives available in AWS, including VPCs, subnets, and security groups. We saw how we can use these to limit the traffic we allow to our EC2 instances and other networked resources. In this chapter we’ll take that even further, looking at more advanced ways of securing networks.
One of the benefits of VPC peering, which we talked about in chapter 5, is that it allows you to route traffic between resources without going over the public internet. In this chapter we’ll talk more about the issues around routing traffic over the public internet and two additional ways of avoiding it.
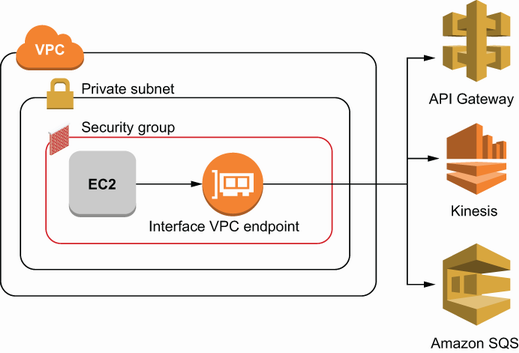
The first way deals with privately connecting to an AWS service from one of your resources using VPC endpoints. An example would be if you had an EC2 instance that called another AWS service like SQS. Figure 6.1 shows how VPC endpoints fit into the network in that situation, allowing a private instance to connect to various AWS services.