chapter two
This chapter covers
- Key components of a cybersecurity toolkit
- How to choose the right tools
- Designing insightful dashboards
- Statistical analysis for threat detection
- How to integrate AI in security analytics
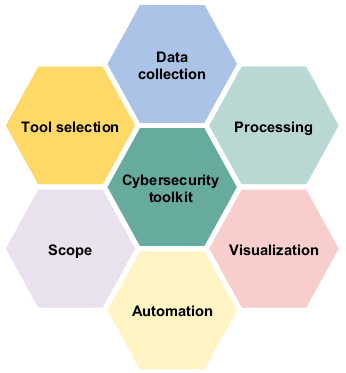
A cybersecurity analytics toolkit consists of multiple integrated tools that work together to support various stages of security analytics. The main components for any specific scope include data collection, processing, visualization, and automation. Each of these tools enhances the efficiency and effectiveness of security teams. Figure 2.1 demonstrates the composition of each toolkit, highlighting how various parts operate within the defined scope.
Figure 2.1 Cybersecurity toolkit consisting of the proper scope, tool selection, data collection, processing, visualization, and automation.