chapter three
3 Implementing and exploiting RNGs
This chapter covers
- Implementing cryptographically secure pseudorandom number generators (CSPRNGs)
- How CSPRNGs can be compromised via weaknesses in their underlying algorithms
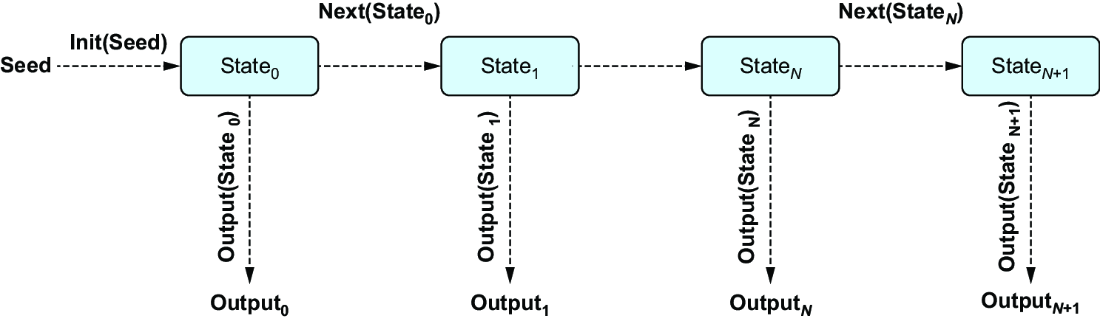
In the previous chapter, we saw how pseudorandom number generators (PRNGs) work in theory. Figure 3.1 shows a PRNG described by three operations:
Init(Seed)transforms the seed to generateState0.Next(StateN)transformsStateNto generateStateN+1.Output(StateN)transformsStateNto generateOutputN.
In this chapter, we will see how these functions are implemented for two widely known RNGs and then write code to exploit them. One is a CSPRNG that was recommended by the National Institute of Standards and Technology (NIST) for almost a decade! (Cryptographic implementations widely rely on algorithms and constants defined by NIST standards.)
Figure 3.1 PRNGs mutate the previous state to generate the next one.