8 Public-key cryptography
This chapter covers
- Understanding asymmetric encryption and its importance
- Using prime numbers in cryptography
- Understanding trapdoor functions
- Understanding public-key cryptography based on the discrete logarithm and integer factorization problems
- Exploiting common factors in RSA keys
- Exploiting short private exponents with Wiener’s attack
Public-key cryptography refers to asymmetric encryption (where encryption and decryption keys are different but related) and digital signatures (where a verifier can verify a correct signature but cannot forge a signature of their own). In this chapter, we tackle the encryption portion of public-key cryptography; the next chapter will focus on digital signatures.
8.1 Asymmetric cryptography: Splitting the secret key into public and private portions
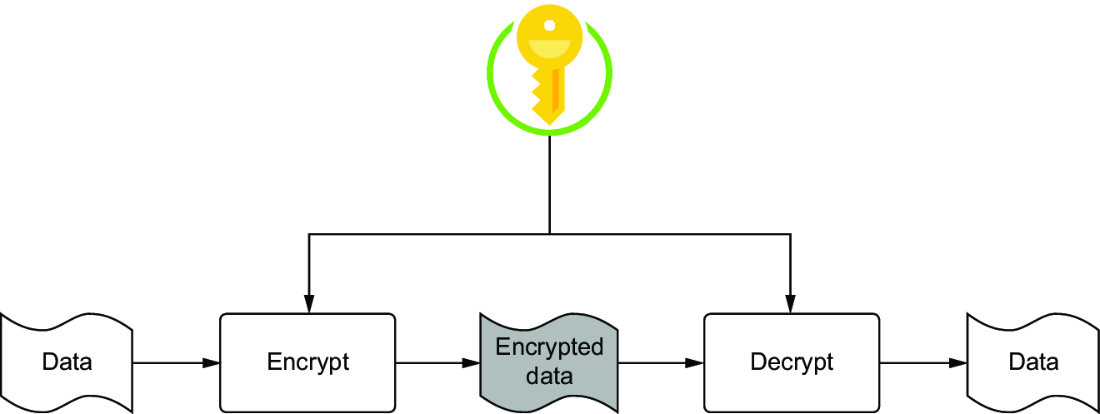
In chapters 4 and 5, we discussed stream ciphers and block ciphers extensively. Together, they represent the two major categories of symmetric-key cryptography. Symmetric refers to the fact that, for example, to provide confidentiality, the same key is used for both encryption and decryption. This key needs to be kept private except between the intended recipients of communication, so this kind of setup is also known as private-key encryption. Figure 8.1 shows the basic principle of symmetric encryption that applies to both block and stream ciphers.
Figure 8.1 Symmetric encryption: the same secret key is used in both encryption and decryption.