Chapter 21. Securing ConfigMgr
In a large organization, many people can use ConfigMgr at the same time for different tasks. For example, some people may be responsible for deploying applications and patches to workstations, and a different team may be performing the same tasks for servers. One team may use ConfigMgr to connect remotely to managed workstations to support users, whereas another team may be responsible for the entire ConfigMgr hierarchy.
Often each member of all of these teams has the same level of internal access to ConfigMgr: Full Administrator. Why? Because it’s considered “easier” to give people more access than they need rather than work out what access they need and provide only that much. Easier, that is, until a desktop admin rolls out Microsoft Office to all the servers, and then management wants to know how that happened (and starts casting bowel-twisting looks in your direction).
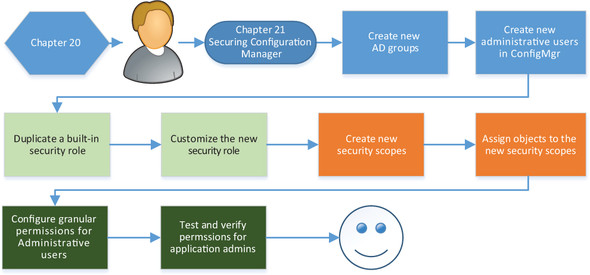
Fortunately, ConfigMgr has a comprehensive and granular internal security structure, and as shown in figure 21.1, you’ll use this to apply the principle of least privilege to all ConfigMgr users.