chapter nine
This chapter covers
- Building Docker images inside Jenkins pipelines and best practices of writing Dockerfiles
- Using Docker agents as an execution environment in Jenkins declarative pipelines
- Integrating Jenkins build statuses into GitHub pull requests
- Deploying and configuring hosted and managed Docker private registry solutions
- Docker images life cycle within the development cycle and tagging strategies
- Scanning Docker images for security vulnerabilities within Jenkins pipelines
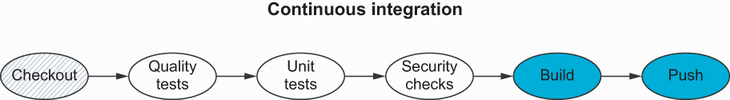
In the previous chapter, you learned how to run automated tests inside Docker containers within CI pipelines. In this chapter, we will finish the CI workflow by building a Docker image and storing it inside a private remote repository for versioning; see figure 9.1.
- Check out the source code from a remote repository. The CI server fetches the code from the version-control system (VCS) on a push event.
- Run pre-integration tests such as unit tests, security tests, quality tests, and UI tests inside a Docker container. These might include generating coverage reports and integrating quality-inspection tools like SonarQube for static code analysis.
- Compile the source code and build a Docker image (automated packaging).
- Tag the end image and store it in a private registry.