In this chapter, you create a useful quantum application. We show that quantum computing allows you to create a secret key that can be shared between two parties in a very secure way. This quantum key distribution (QKD) is the basis for a number of encryption techniques that are proven to be secure—even the best quantum computer can’t break this security!
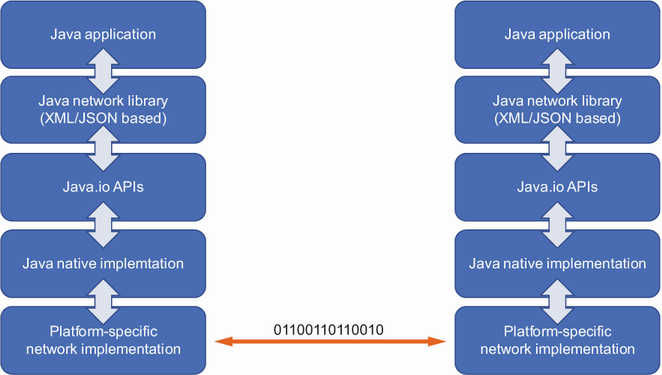
We started chapter 6 by showing how classical networks are used to send classical information from one node (or computer) to another. We explained how different pieces of information travel from Java applications to a low-level implementation, where they are sent as bits to the other node and travel upward again. This is shown in figure 8.1.
In this chapter, we focus on what happens at the communication level between the two nodes. Bits are transferred over a network connection: e.g., over optical fiber.