1 Making Sense of Application Security
This chapter covers
- Why learning security is important
- The consequences of poor security practices
- What are the roles in the information security field
- Identifying the security skills you should possess as an application developer
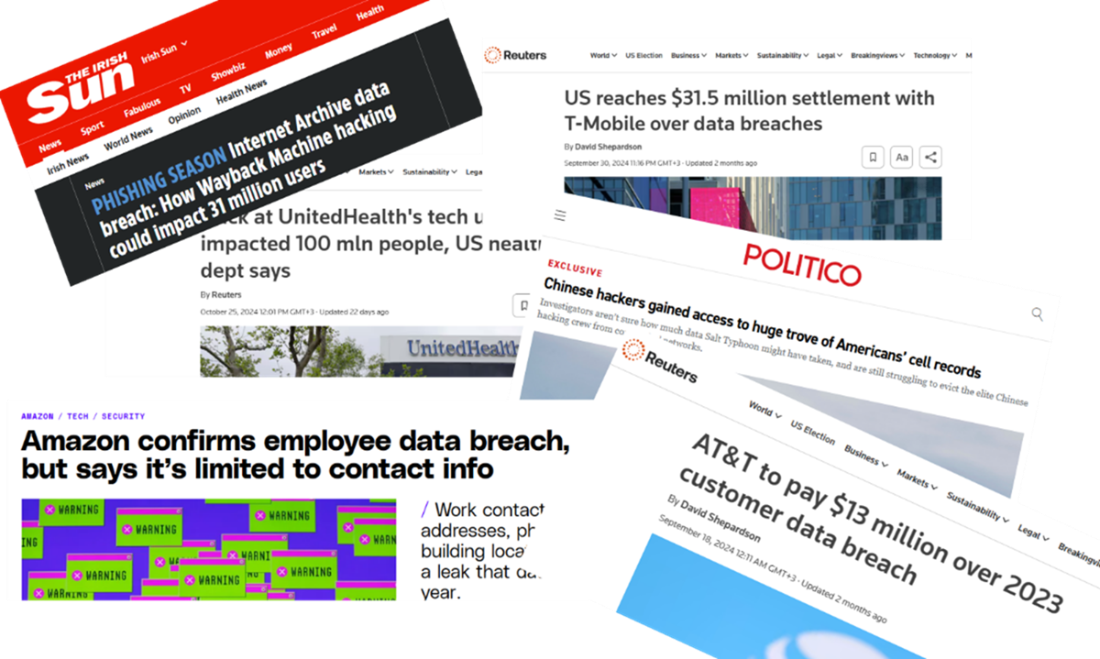
Every week we are treated to a headline about some security vulnerability in a widely used piece of software or a data breach at a mega-corporation affecting millions of users (figure 1.1). My bank replaced my credit card twice in a five-year period due to data breaches at large retailers where I shopped.
Figure 1.1 Headlines showcasing major recent data breaches and security vulnerabilities, emphasizing the widespread impact on millions of users and the persistent threat to digital security.
We used to think that security vulnerabilities are primarily a software issue. However, hardware security vulnerabilities have been common in recent years. The Meltdown and Specter vulnerabilities, disclosed in January 2018, allowed attackers to bypass CPU hardware protections and gain unauthorized memory access (https://meltdownattack.com/). In a cloud or multi-tenant environment, Meltdown and Specter make it possible for one cloud tenant to see the memory of another tenant. The hardware walls we depend on to isolate workloads were suddenly full of holes for attackers to sneak through.